© Silas Stein / Global Look Press
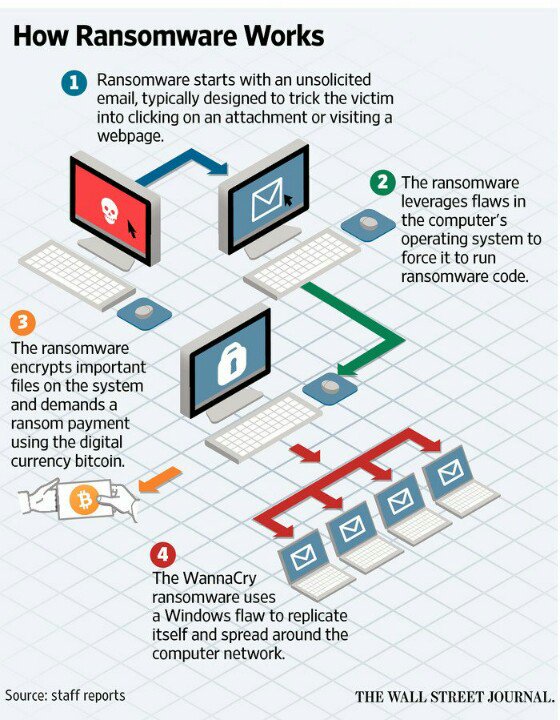
With the help of leaked software developed by the National
Security Agency (NSA), malicious ransomware called the Wanna Decryptor –
or WannaCry – spread to 150 countries until Mei, 15.
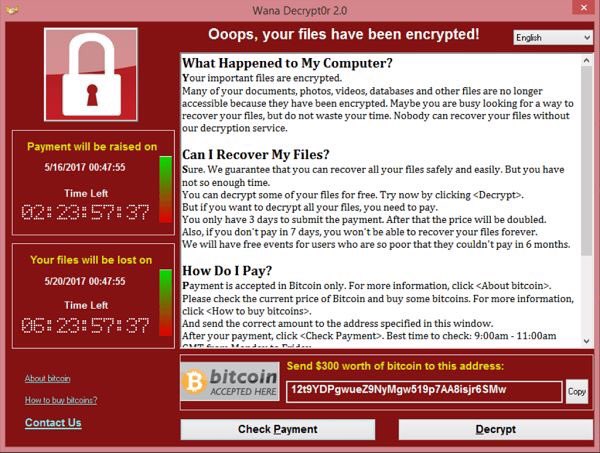
The malware instructs people to pay up to £460 to one of three bitcoin addresses in order to retain their files, and also displays a countdown clock giving a deadline for the payments.
The hackers, who have locked files on 200,000 computers worldwide, have only made around $500,000 so far, despite the magnitude of the attack. Britain’s National Crime Agency (NCA) is urging victims not to pay the ransom.
Nothing has yet been withdrawn from any of the bitcoin accounts, and law enforcement agencies watching them say the perpetrators could be difficult to trace until they access some of the ransom money.
Ransomware bounties are usually paid in bitcoin, a digital currency that keeps its users anonymous. Bitcoin is also traceable, however, as every transaction is tied to publicly-accessible accounts, typically called wallets. The wallets show each payment that victims have sent in hopes of regaining access to their files.
New payments are coming in regularly, according to Ransom Tracker, a Twitter bot that is sending out automated messages and posting every time a payment is made to one of the three bitcoin addresses.
“Cybercriminals may believe they are anonymous but we will use all the tools at our disposal to bring them to justice,” he told the Times.
Rob Wainwright, the director of Europol, told the newspaper that security officials believe the hack is the work of criminals, rather than a state-sponsored attack.
“Our working assumption, as with every other major ransomware attack, is that this is a cybercriminal attack. Unless we have something definitive to point us in another direction that’s our assumption at the moment. As in any investigation, we keep our mind open.”
Public awareness is “absolutely critical for preventing cyberattacks,” Neil Walsh, the head of the Global Program on Cybercrime launched by the UN Office on Drugs and Crime (UNODC), told. “Such threats could theoretically be averted if the public is aware of what a cyberattack looks like and is [cautious] with opening emails and especially emails with attachments that they were not expecting to get,” he said.
At the same time, he warned that the WannaCry ransomware could potentially “propagate further” as people around the world got back to work Monday.
He went on to call on all countries to join their efforts in combating cyberthreats “irrespective of politics and politicizing.” He also urged the governments to “use law enforcement channels such as Interpol, Europol and bilateral cooperation as well as to work together politically to help to mitigate these threats.”
On Sunday, Europol Director Rob Wainwright told the ITV network that the cyberattack that began on Friday has hit some 200,000 victims in over 150 countries so far.
“The global reach is unprecedented. The latest count is over 200,000 victims in at least 150 countries, and those victims, many of those will be businesses, including large corporations,” he said.
“At the moment, we are in the face of an escalating threat. The numbers are going up; I am worried about how the numbers will continue to grow when people go to work and turn [on] their machines on Monday morning,” he added.
WannaCry 2.0 arrives with no kill switch
#WannaCry #WannaCry2
Tech giant Microsoft recently lashed out at NSA for the role it played in the chain of events that led to the recent WannaCry epidemic.
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world,” Microsoft President and Chief Legal Officer Brad Smith said in a blog post on Sunday.
“This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem.”
Hackers collecting bitcoin following Friday’s cyberattack have
not yet withdrawn any of the digital currency from their accounts, and
could have a hard time doing so without getting caught, experts say.
The malware instructs people to pay up to £460 to one of three bitcoin addresses in order to retain their files, and also displays a countdown clock giving a deadline for the payments.
The hackers, who have locked files on 200,000 computers worldwide, have only made around $500,000 so far, despite the magnitude of the attack. Britain’s National Crime Agency (NCA) is urging victims not to pay the ransom.
Nothing has yet been withdrawn from any of the bitcoin accounts, and law enforcement agencies watching them say the perpetrators could be difficult to trace until they access some of the ransom money.


Ransomware bounties are usually paid in bitcoin, a digital currency that keeps its users anonymous. Bitcoin is also traceable, however, as every transaction is tied to publicly-accessible accounts, typically called wallets. The wallets show each payment that victims have sent in hopes of regaining access to their files.
New payments are coming in regularly, according to Ransom Tracker, a Twitter bot that is sending out automated messages and posting every time a payment is made to one of the three bitcoin addresses.
[2017-05-15 14:20:47] Ransom paid to #WannaCry: 0.18BTC = $314 (https://t.co/qfSLWet6Dj).— Ransom Tracker (@ransomtracker) May 15, 2017
WannaCry total: 31.39BTC = $54,140.
What you need to know about #Bitcoin after the WannaCry ransomware attack https://t.co/PGa55BNjXL pic.twitter.com/9iDhlF0KaM— Bitcoin_Friend (@Bitcoin_Friend) May 15, 2017
Oliver Gower, the deputy director of the NCA’s national cybercrime unit, has vowed to track down the hackers.This is how #WannaCry is being shown on German television. @SwiftOnSecurity @hackerfantastic @x0r @lumines pic.twitter.com/v9jOCy8ct6— Dennis MH (@D2KX_) May 15, 2017
“Cybercriminals may believe they are anonymous but we will use all the tools at our disposal to bring them to justice,” he told the Times.
Rob Wainwright, the director of Europol, told the newspaper that security officials believe the hack is the work of criminals, rather than a state-sponsored attack.
“Our working assumption, as with every other major ransomware attack, is that this is a cybercriminal attack. Unless we have something definitive to point us in another direction that’s our assumption at the moment. As in any investigation, we keep our mind open.”
Public awareness is “absolutely critical for preventing cyberattacks,” Neil Walsh, the head of the Global Program on Cybercrime launched by the UN Office on Drugs and Crime (UNODC), told. “Such threats could theoretically be averted if the public is aware of what a cyberattack looks like and is [cautious] with opening emails and especially emails with attachments that they were not expecting to get,” he said.
At the same time, he warned that the WannaCry ransomware could potentially “propagate further” as people around the world got back to work Monday.
People still refuse to accept the sad truth #WannaCry pic.twitter.com/NviBJcozm5— Florian Roth (@cyb3rops) May 15, 2017
“A challenge with any ransomware or cyberattack is that when people come back to work they turn on potentially insecure systems, which are not updated with the latest security patches. Perhaps, they are unaware of how this threat arises through email or opening attachments,” Walsh said.VIDEO: More than 200,000 victims in 150 countries have been the target of a cyber attack called #ransomware. #WannaCry pic.twitter.com/qLh8OFTMdp— dwnews (@dwnews) May 15, 2017
He went on to call on all countries to join their efforts in combating cyberthreats “irrespective of politics and politicizing.” He also urged the governments to “use law enforcement channels such as Interpol, Europol and bilateral cooperation as well as to work together politically to help to mitigate these threats.”
On Sunday, Europol Director Rob Wainwright told the ITV network that the cyberattack that began on Friday has hit some 200,000 victims in over 150 countries so far.
“The global reach is unprecedented. The latest count is over 200,000 victims in at least 150 countries, and those victims, many of those will be businesses, including large corporations,” he said.
“At the moment, we are in the face of an escalating threat. The numbers are going up; I am worried about how the numbers will continue to grow when people go to work and turn [on] their machines on Monday morning,” he added.

WannaCry 2.0 arrives with no kill switch
Tech giant Microsoft recently lashed out at NSA for the role it played in the chain of events that led to the recent WannaCry epidemic.
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world,” Microsoft President and Chief Legal Officer Brad Smith said in a blog post on Sunday.
“This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem.”
2.7 - WannaCry Ransomware: Microsoft Calls Out NSA For 'Stockpiling' Vulnerabilities : The Two-Way : NPR https://t.co/UdFSzLuGlS— Alatitude77-infosec (@AL77_infosec) May 15, 2017
Theft of the insidious software was reported in April. Who deployed it now is unknown. It's hit U.S., Asia, Europe. https://t.co/dB6JcVN1wv— NPR (@NPR) May 15, 2017


Post a Comment Blogger Facebook Disqus